Reviewing GitHub Advanced Security scan results
We now have GitHub Advanced Security running on our Juice Shop repository, andshould already have a few results. Before we look, let’s take a few steps to generate some more results so we can see GitHub Advanced Security’s protections in action. Then we’ll review our scan results and learn about some of the actions we can take in response.
TELUS will once again share some best practices.
In this guide, you will learn:
How to view Dependabot, code scanning, and secret scanning results
How to dismiss false positive results in secret scanning
How to automatically patch vulnerabilities with Dependabot
1. Add an invalid secret to the Juice Shop repository.
Open the README.md file from your Juice Shop repository.
Paste in the following secret (don't worry, it's already been invalidated, it won’t work) anywhere in the document:
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
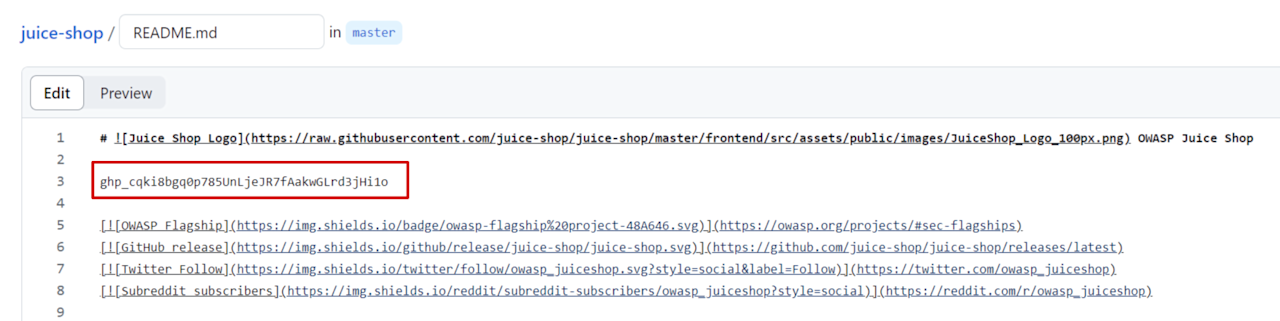
Commit the changes.
You'll receive a "Secret Detected" message informing you that push protection for secrets found an GitHub Personal Access Token on a specific line of the file.
You’ll have the choice to either cancel the commit or allow the secret by selecting one of the following three options:
It's used in tests
It's a false positive
I'll fix it later
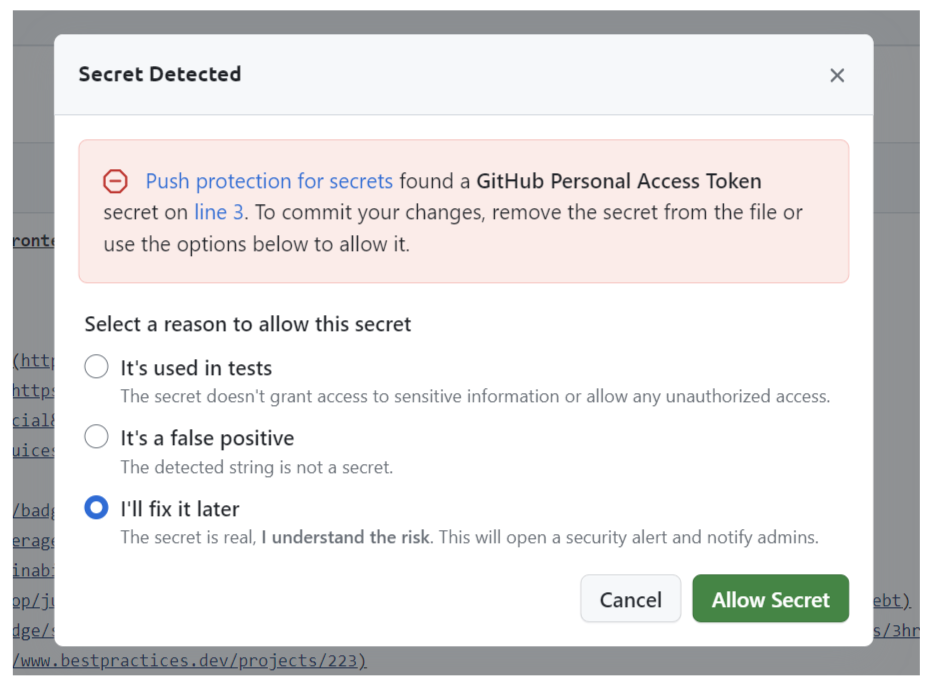
These options make it possible to move forward even when push protection detects a potential secret. If you do commit a secret, the reason you select here is logged for future review.
We want to view the alert that secret scanning will generate, so select I'll fix this later then Allow Secret. Commit the change.
The I’ll fix this later option should be used sparingly, if at all. It will prompt you to enter a reason that you’re committing the secret now, and create a log so that the reason can be reviewed in the future. GitHub also creates alerts both in secret scanning and by email for the commit author, repository administrator, security managers, and anyone else who opts in to email alerts.
2. View the Dependabot alerts.
On your Juice Shop repository’s GitHub.com page, click Settings under your repository name. If you cannot see the Security tab, select the “...” dropdown menu, then click Security.
Click the Dependabot section on the sidebar.
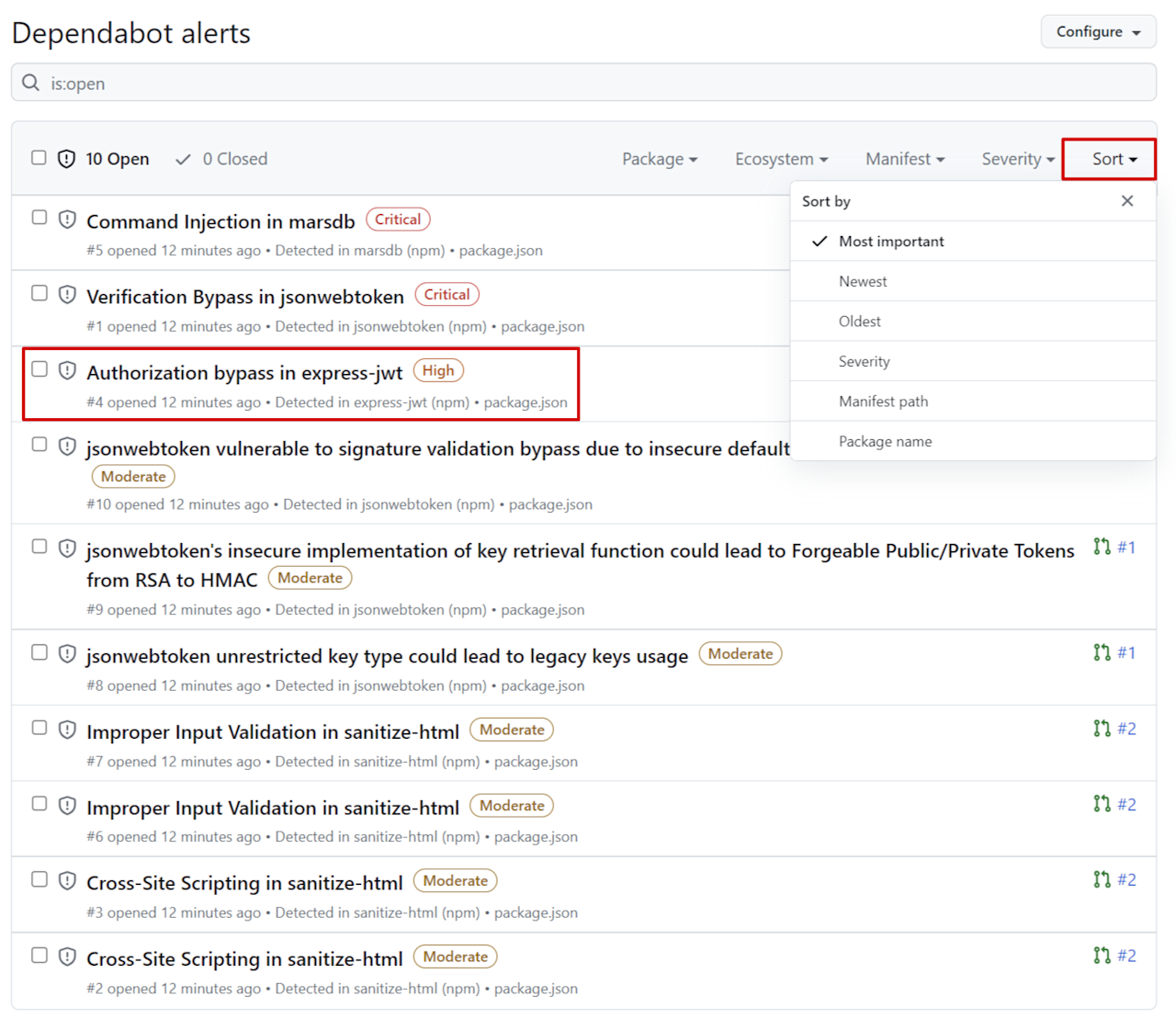
There should be a list of results, with the most critical alerts at the top.
You can filter these results by Package, Ecosystem, Manifest, or Severity, and sort by priority, date, severity, and more. You can create different views and bookmark the URLs to come back to them.
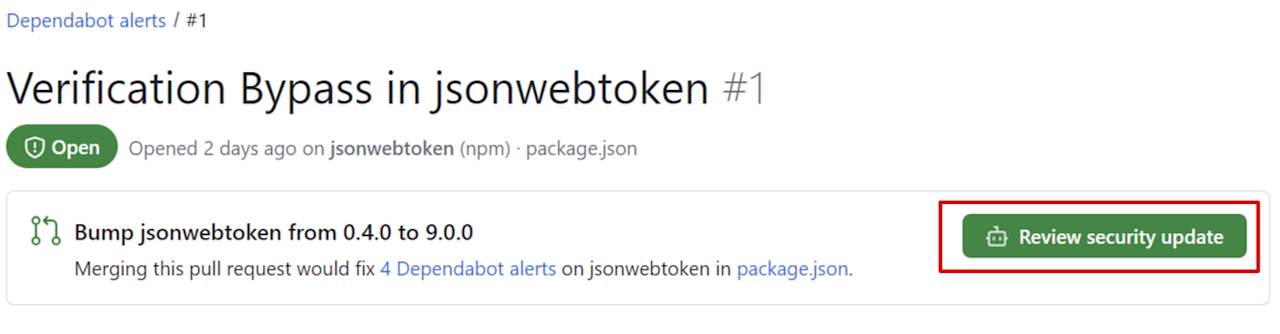
What developers really want to know, however, is how to remediate an issue. Click the Verification Bypass in jsonwebtoken alert.
The Review security update button means a patch is available for this vulnerability. Click it to automatically create a pull request to fix the problem.
3. View code scanning results.
On your Juice Shop repository’s GitHub.com page, click Security under your repository name. If you cannot see the Security tab, select the “...” dropdown menu, then click Security.
Click Code scanning on the sidebar.
There should be a status notification at the top of this page to let you know the tool is working.
Just as in our Dependabot results, there should be a list of vulnerabilities, ordered by criticality. And once again you can filter or sort these based on several criteria, including language, tool, and branch, or sort them based on date created or date updated.
Click the first Code injection alert.
Everything on the page for this alert is designed with remediation in mind. There's an explanation of the problem and a recommended way to fix it, complete with language-specific code examples.
Follow the Show paths link. This displays an end-to-end data flow showing where the vulnerability starts and where it finishes.

4. View secret scanning results.
On your Juice Shop repository’s GitHub.com page, click Security under your repository name. If you cannot see the Security tab, select the “...” dropdown menu, then click Security.
Click Secret scanning on the sidebar.
There should be just one alert for the invalid GitHub Personal Access Token we introduced earlier. As you can see, the results don't just tell you that a secret was found, but the specific type of secret.
Click this alert.
The alert page contains information on where the secret was found, in this case within the README.md file, and some recommendations on how to remediate the issue.
Click the secret. From here you can see that we bypassed this secret alert earlier, and when we did that.
6. View the Security overview.
Go to your organization page on GitHub.com and click the Security tab. If you cannot see the Security tab, select the “...” dropdown menu, then click Security.
From here you can see alerts from Dependabot, code scanning, or secret scanning for every repository in your organization. You can view alerts by risk level or based on the tool that generated them. You can also check which repositories are and are not currently protected by GitHub Advanced Security, and view metrics such as mean time to remediation (MTTR) and how many secrets have been blocked or bypassed.
Up Next: Essentials of GitHub Advanced Security module wrap-up
Let’s review what we’ve learned so far and take a look at what else we can do with GitHub Advanced Security.